Connect Google Cloud resources
Google Cloud resources are organized hierarchically. You can use Google Cloud's Identity and Access Management (IAM) system to assign granular access to specific resources and prevent unwanted access to others. The IAM policy hierarchy follows the same path as the Google Cloud resource hierarchy.
To offer the full capabilities of the DoiT platform, we require permissions at different levels to access the Google API and obtain information for monitoring or alerts, and help you act on recommendations if applicable. See Security and data access policy: Feature permissions for details.
Required permissions
To connect Google Cloud resources with the DoiT console:
-
Your DoiT account must have the Manage Settings permission.
-
To connect a Google Cloud Organization, you must have been granted the Organization Role Administrator (
roles/iam.organizationRoleAdmin) IAM role on the organization. You need this role to create and attach custom roles to service accounts under the organization. -
To connect a Google Cloud project that is not part of an already connected organization, you must have been granted the Role Administrator (
roles/iam.RoleAdmin) IAM role on the project. You need this role to create and attach custom roles to service accounts under the project. -
To connect a BigQuery dataset for insights from Google Cloud Recommender BigQuery Export, you must have been granted the Role Administrator (
roles/iam.RoleAdmin) IAM role on the project that hosts the dataset. You need this role to create and attach custom roles to service accounts under the project.
Note that at the moment, most of the DoiT features require permissions at the organization level. Only a small set of feature and core functionality permissions can be granted at the project level.
Service account authentication
Google Cloud supports using service accounts as identities for workloads. Starting June 2023, the preferred way to authenticate the service account for DoiT console workloads changes to service account impersonation, which mitigates the security risks associated with service account keys.
Service account impersonation involves two principals:
-
The privilege-bearing service account that has the required permissions to access the target resource.
-
The caller that needs to access the target resource but lacks permissions.
Configure identities for DoiT workloads
When connecting the DoiT console, you mainly need to perform two tasks to configure the identities for DoiT workloads:
-
Task 1: Create a privilege-bearing service account with permissions to access the target resources.
-
Task 2: Grant the DoiT-owned service account
[email protected](caller) theServiceAccountTokenCreatorrole, allowing it to impersonate the privilege-bearing service account.NoteIf you use GCP organization policy to restrict identities by domain, make sure to allowlist the DoiT caller service account using its Organization Resource ID
C03rw2ty2.
Below are the detailed configuration steps:
-
Sign in to the DoiT console, select Integrate from the top navigation bar, and then select Google Cloud.
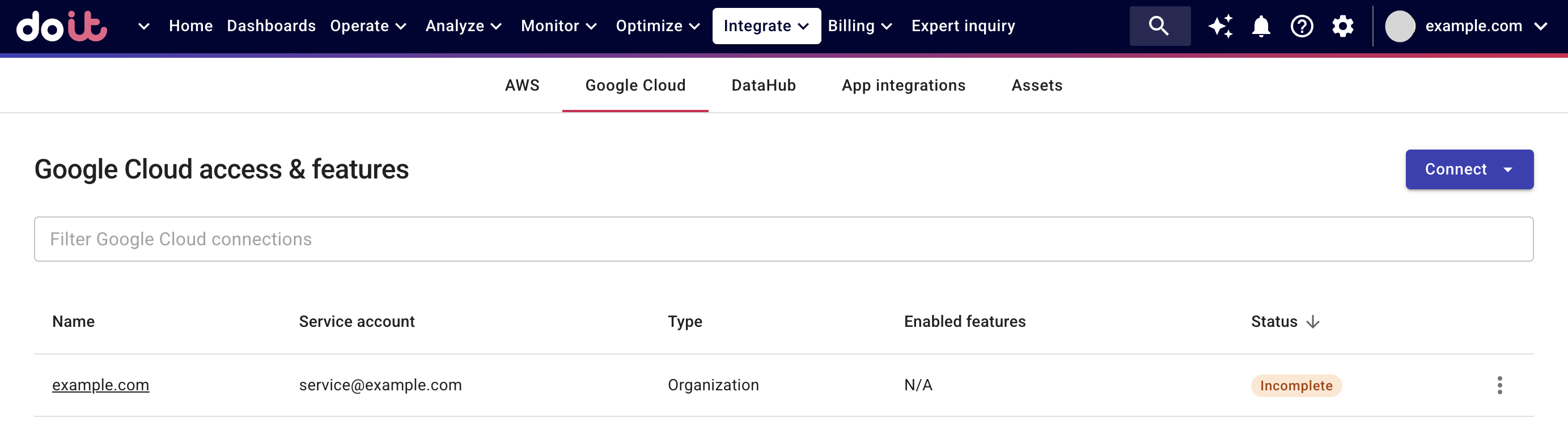
-
Continue with the section specific to your target resource type:
Connect an organization
-
From the Connect drop-down, select Organization.
-
Select the features you want to enable for the organization. You can expand features to view the required permissions.
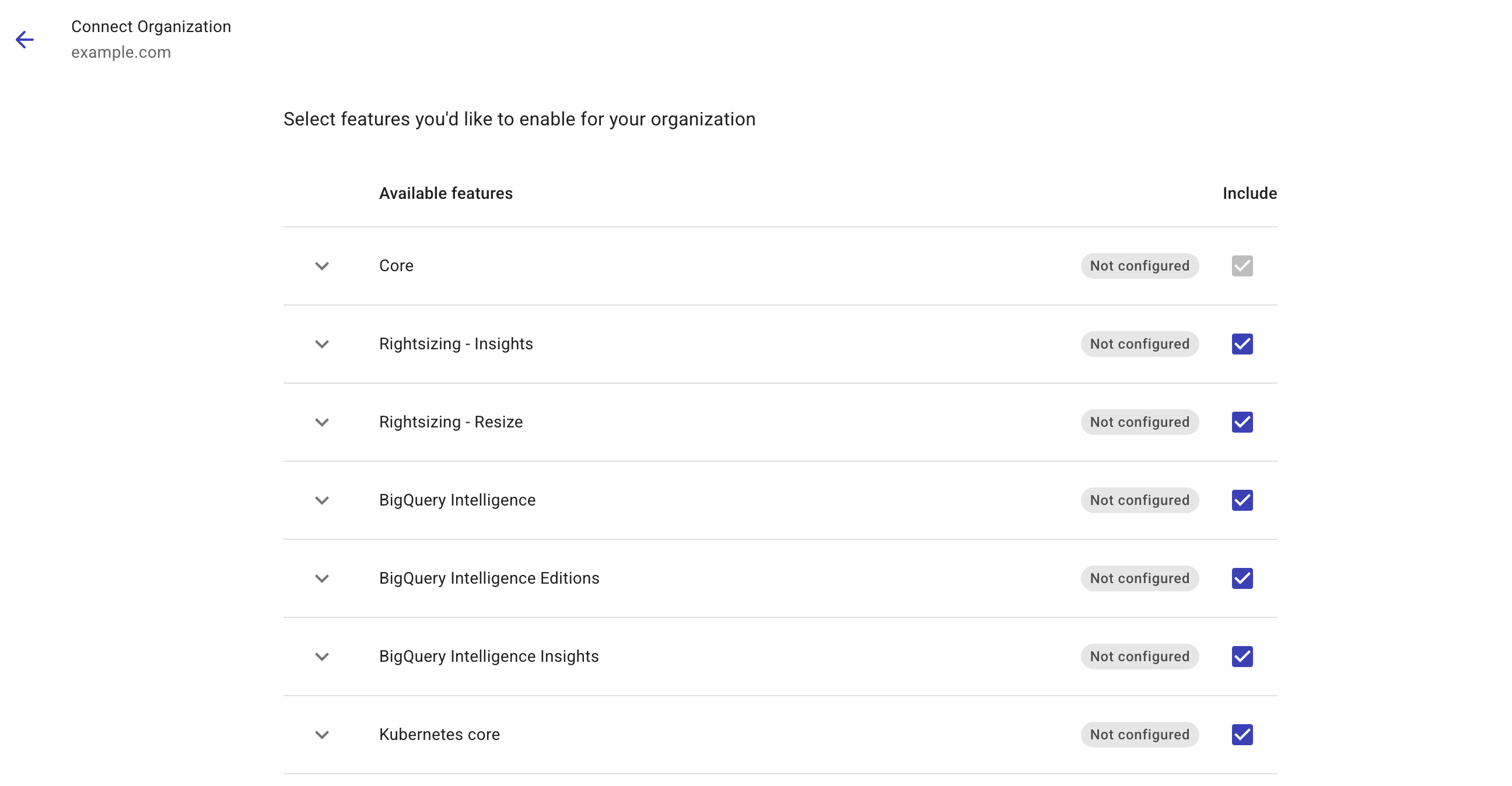
-
Select Generate gcloud commands. The generated gcloud commands you need to run are displayed in the DoiT console.
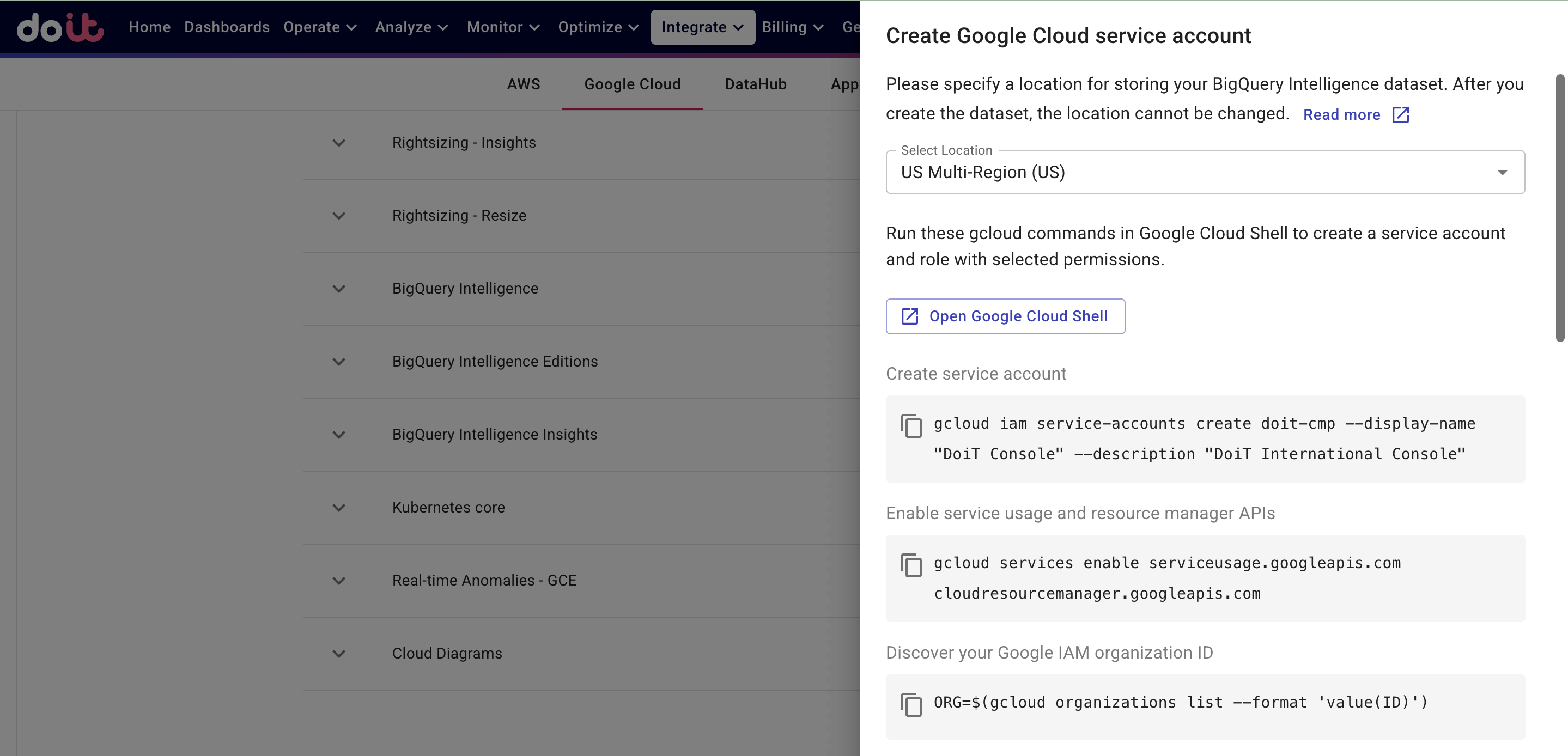
-
Select a location to store your BigQuery Intelligence dataset.
-
Launch a Google Cloud Shell session.
-
Select a Google Cloud project that meets the following conditions:
-
The project belongs to your organization.
-
The project is connected to a Google Cloud Billing account (see Verify the billing status of your projects).
-
You intend to keep the project for the long term and restrict its access only to trusted people.
-
-
Configure access control for the organization by running the commands provided in the DoiT console sequentially:
-
Create a new service account in the current project.
-
Enable service usage API and resource manager API in the current project.
-
Get your Google IAM organization ID.
-
Create a custom role named
doit_cmp_rolewith the permissions required by your chosen features, then add a policy binding to attach the role to the new service account under the organization. Permissions are granted at the organization level. -
Add an IAM policy binding to attach the role
roles/iam.serviceAccountTokenCreatorto the DoiT caller service account, allowing it to impersonate the privilege-bearing service account.
-
-
Sign in to the Google Cloud console, go to the Roles page and verify that you have created a
doit_cmp_rolelinked to the DoiT service account in your organization.
Connect a project
This section applies in the following situations:
-
You want to connect a Google Cloud project that doesn't belong to an already connected organization.
-
You want to connect a dataset to display insights from GCP Recommender BigQuery export in DoiT Insights.
-
You want to enable real-time anomaly detection for BigQuery.
To connect an project:
-
From the Connect drop-down, select Project.
-
Select the features you want to enable for your project. You can expand features to view the required permissions.
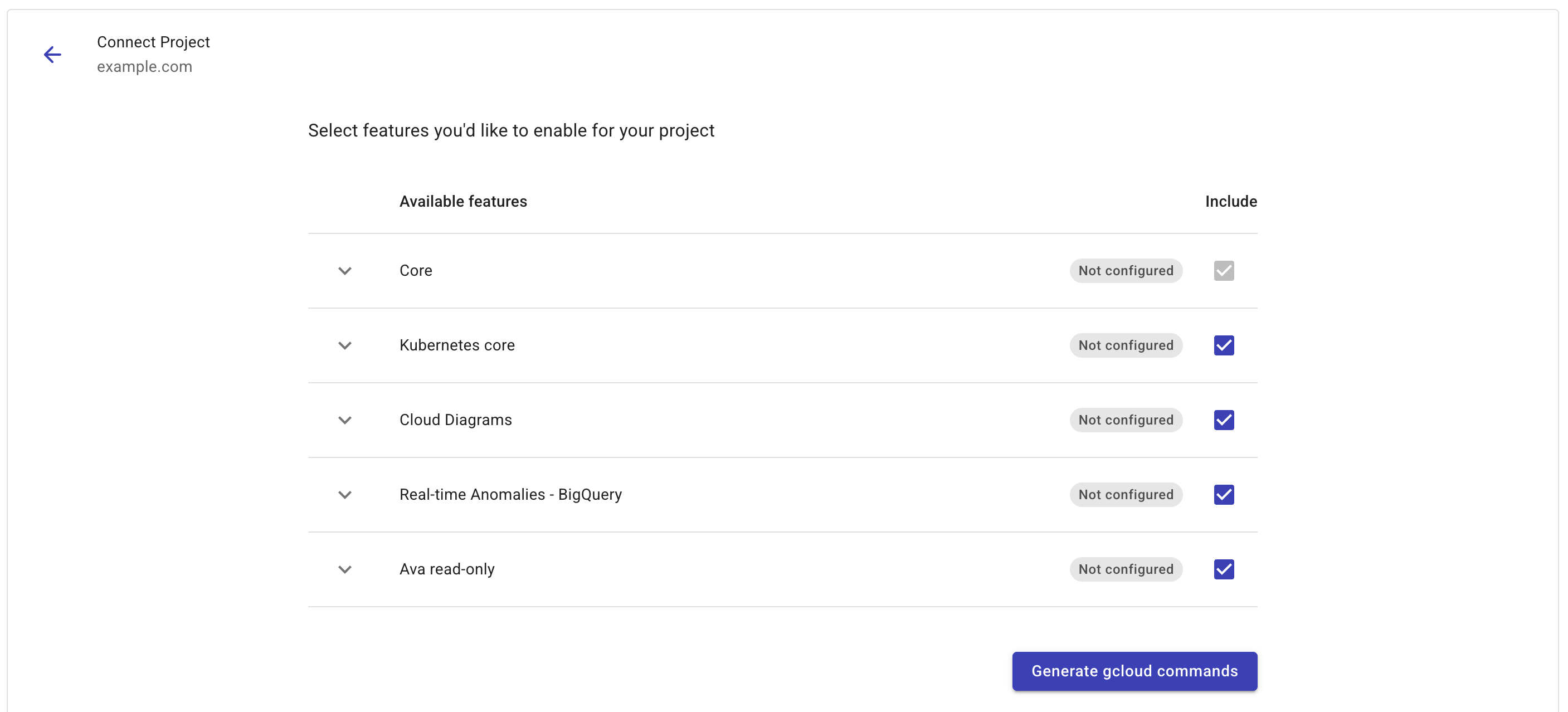
-
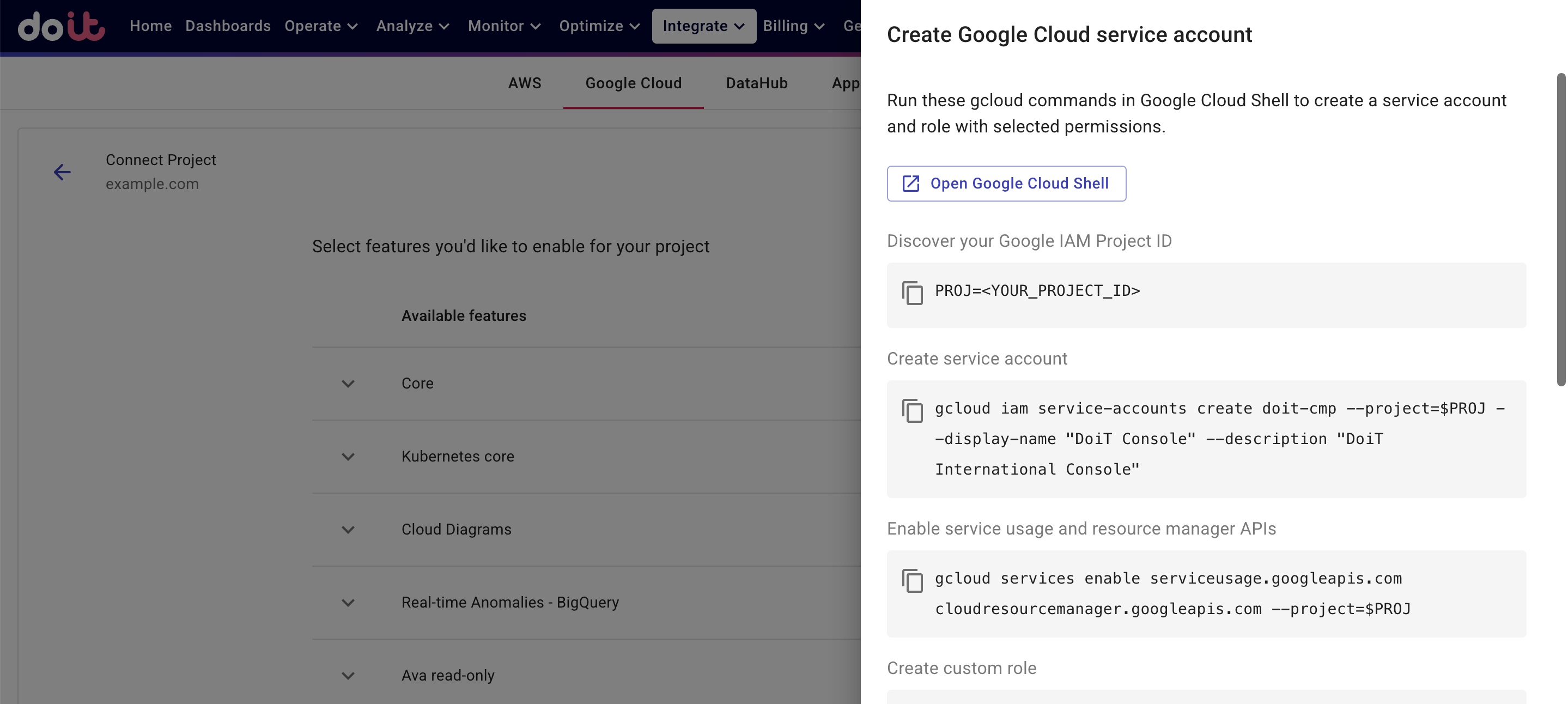
Select Generate gcloud commands. The generated gcloud commands you need to run will be displayed in the DoiT console.
-
Get your Google IAM Project ID. See Identifying projects.
-
Launch a Google Cloud Shell session and select the project you want to connect.
-
Configure access control for the project by running the commands provided in the DoiT console sequentially:
-
Set the project ID.
-
Create a new service account in the project.
-
Enable service usage API and resource manager API in the project.
-
Create a custom role named
doit_cmp_rolewith the permissions required by your chosen features, then add a policy binding to attach the role to the new service account. Permissions are granted at the project level. -
Add an IAM policy binding to attach the role
roles/iam.serviceAccountTokenCreatorto the DoiT caller service account, allowing it to impersonate the privilege-bearing service account. -
Download the service account details to a file named
doit_cmp_sa_details.json, then select Upload file in the DoiT console to upload the file.
-
-
Sign in to the Google Cloud console, go to the Roles page and verify that you have created a
doit_cmp_rolelinked to the DoiT Service Account in your project.
Connect a dataset
To enable insights from GCP Recommender BigQuery export, you must connect the BigQuery dataset that contains the insights and recommendations data.
Proceed only if you meet all the prerequisites listed below:
-
The insights and recommendations data from Google Cloud Recommender have been exported to the BigQuery dataset.
-
You have enabled the Core feature when connecting your organization.
-
You have enabled the Core feature when connecting the project that hosts the BigQuery dataset.
-
From the Connect drop-down, select Dataset.
-
Select the checkbox of Insights from GCP Recommender BigQuery export. You can expand the feature to view the required permissions.
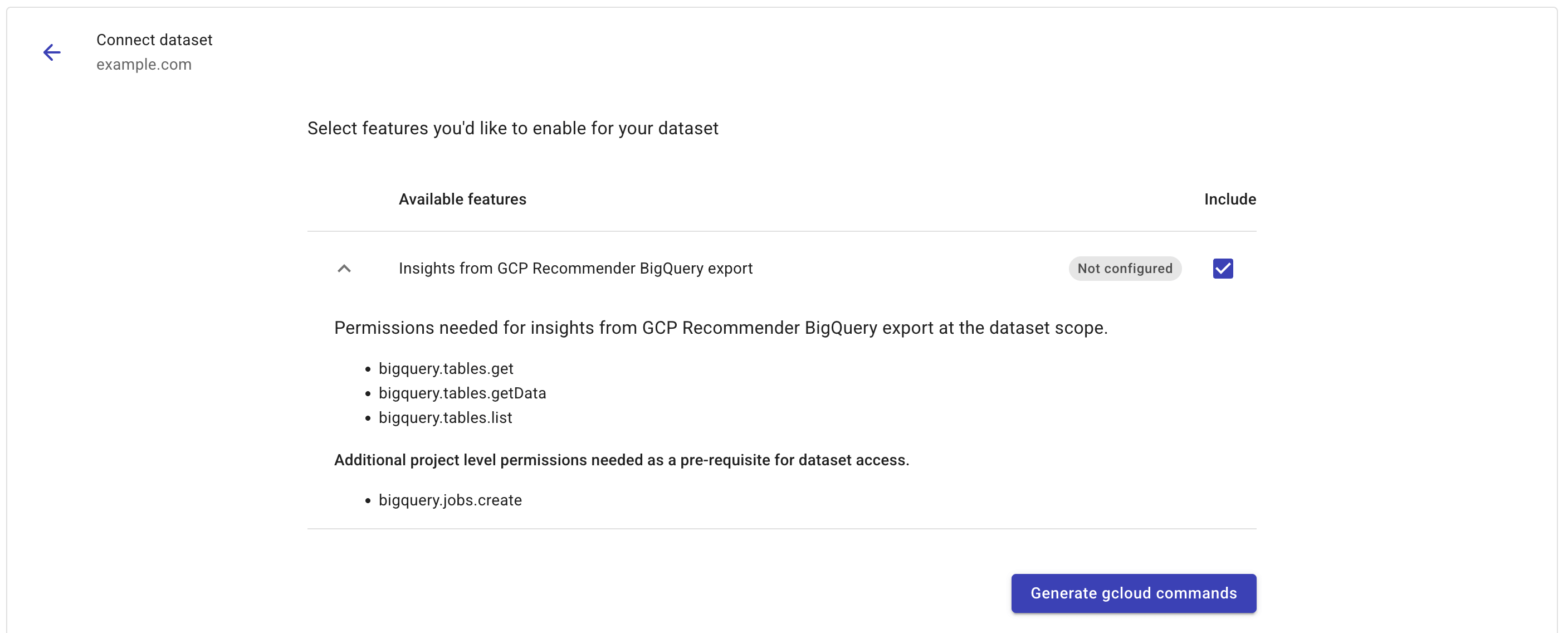
-
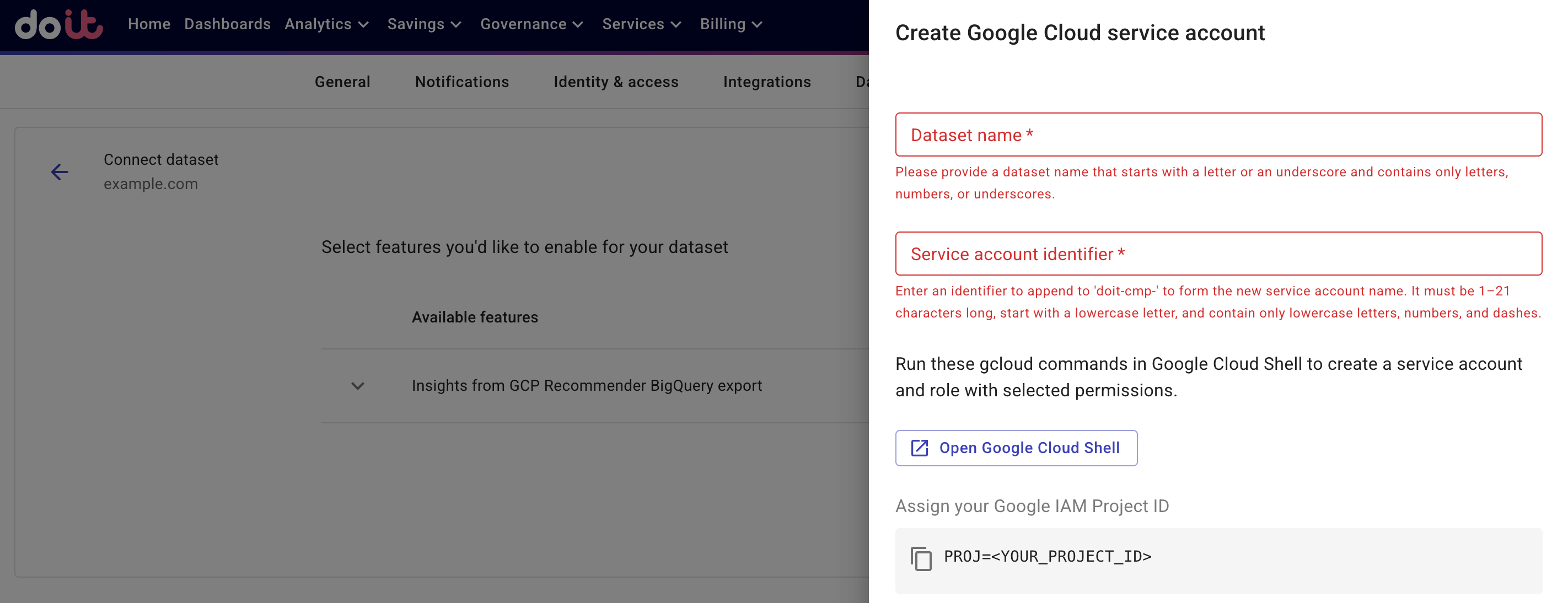
Select Generate gcloud commands to display the instructions and gcloud commands you need to run.
-
Provide the dataset name and an identifier to form the new service account. Make sure to follow the naming conventions displayed in the DoiT console.
-
Get your Google IAM Project ID. See Identifying projects.
-
Launch a Google Cloud Shell session and select the project that hosts the dataset.
-
Configure access control for the BigQuery dataset resource by running the commands provided in the DoiT console sequentially:
-
Set the project ID.
-
Create a new service account for the dataset access.
-
Create a custom role named
doit_cmp_dataset_project_access_rolewith project-level permissions, then Add a policy binding to attach the role to the service account. -
Create a custom role named
doit_cmp_dataset_access_rolewith dataset-level permissions, then update the dataset IAM policy to attach the role to the service account. -
Add an IAM policy binding to attach the role
roles/iam.serviceAccountTokenCreatorto the DoiT caller service account, allowing it to impersonate the privilege-bearing service account.
-
-
Download the service account details to a file named
doit_cmp_dataset_sa_details.json, then select Upload file in the DoiT console to upload the file. -
Sign in to the Google Cloud console, go to the Roles page and verify that you have created two custom roles (
doit_cmp_dataset_project_access_roleanddoit_cmp_dataset_access_role) linked to the DoiT Service Account in your project.
Update role
To add or remove features for a resource:
-
Select Integrate from the top navigation bar, and then select Google Cloud.
-
Select the kebab menu (⋮) next to the resource you want to update, and then select Edit.
-
Modify the selection of features as needed.
-
Select Generate gcloud commands.
-
Follow the instructions displayed in the side panel to update your custom role.
Connect multiple resources
-
If you have multiple Google Cloud organizations or projects, connect each separately to regulate which organization or project has access to specific features.
Note that BigQuery Intelligence doesn't support multiple service accounts at the moment. See Set up BigQuery Intelligence.
-
If you connect multiple BigQuery datasets for insights and recommendations, DoiT Insights will generate insights based on data in all the connected datasets.
Remove a connection
To remove a connected organization, project, or dataset.
-
Select the kebab menu (⋮) next to the resource you want to disconnect.
-
Select Delete connection.
Remove service accounts
In case you need to remove a service account under a connected organization from the DoiT console and then create a new one, be aware that:
-
Removing a service account from the DoiT console also removes the related datasets and sinks created by BigQuery Intelligence.
-
Once the BigQuery Intelligence permissions are granted to the new service account, we'll re-create the sink and trigger historical jobs backfill, which may lead to increased costs during your service account setup.